HEATMAP_ANALYSIS_V1 (Grafana + Loki Honeypot Analysis)
HEATMAP_ANALYSIS_V1 (Grafana + Loki Honeypot Analysis)
Padroes de ataques e visualizacao de ataques de um honeypot, o que isso fala para nos?
[ 0x00 ] INITIAL_LOG_BOOT
O que você está vendo no dashboard não é um mapa de "hackers de filme" digitando em telas verdes. É o ruído da internet. Se você levanta um IP público hoje, você não está mais "sozinho". Em menos de 60 segundos, algum script na China, na Rússia ou num datacenter em Ohio vai te encontrar e isso é o comum.
Este artigo é uma autópsia técnica do que esse calor vermelho realmente significa. A toca do coelho é feita de scripts automatizados e instâncias de nuvem mal configuradas.
[ 0x01 ] THE_CLOUD_ABUSE_BIAS
Aquele brilho intenso na Costa Leste dos EUA (regiões us-east-1) é o coração da AWS. Mas não se engane: não são os funcionários da Amazon te atacando.
O que acontece é o "Cloud-Hopping". Atacantes usam cartões de crédito clonados ou instâncias com vulnerabilidades de kernel para subir proxies de alta banda. Uma VPS de 5 dólares tem conexão de 1Gbps; seu roteador da Vivo tem... bem, você sabe. É muito mais eficiente escanear o IPv4 inteiro a partir de um backbone de datacenter do que de uma rede residencial. (A não ser que você tenha 1001 redes residenciais :p)
[ 0x02 ] THE_FLAP-D_PARADOX (EUROPE)
Londres, Amsterdã, Frankfurt, Paris e Dublin. O eixo FLAP-D é onde a internet europeia respira. A concentração de ataques aqui é puramente estatística: é onde estão os maiores IXPs (Internet Exchange Points) e os datacenters de baixa latência como Hetzner e OVH.
As botnets adoram esses caras porque a reputação do IP demora a cair. Eles conseguem disparar milhões de pacotes de brute-force antes que o provedor receba os primeiros reports de abuso e derrube a instância.
[ 0x03 ] THE_IOT_PLAGUE: MIRAI & BEYOND
Enquanto a nuvem foca em brute-force pesado, o calor no Sudeste Asiático e em São Paulo vem de algo mais... "sujo". Estamos falando de IoT Botnets.
Roteadores de padaria, câmeras IP baratas, DVRs que nunca viram um update de firmware. Malwares como Mirai, Aisuru e o recente P2PInfect (que usa exploits em Redis) transformam esses dispositivos em zumbis. Eles não têm a banda de uma AWS, mas têm o número.
* Behavior: O bot entra, tenta senhas padrão (admin/admin, root/123456), se entrar, ele mata outros malwares que já estavam lá e "fecha a porta" pra ele. É uma guerra territorial pelo seu roteador.
[ 0x04 ] CASE_STUDY: SÃO_PAULO_CLUSTER
O Brasil é um dos maiores geradores de "ruído" do mundo. Em São Paulo, a densidade de conexões residenciais com configurações de segurança inexistentes é um prato cheio.
Nos nossos honeypots (Cowrie para SSH e Dionaea para malware), o primeiro hit de brute-force TCP geralmente vem em menos de 45 segundos. A maioria das tentativas foca em portas clássicas: 22 (SSH), 23 (Telnet), 3389 (RDP) e 5060 (SIP). Eles não querem seus arquivos; eles querem seu processamento para minerar Monero ou participar de um ataque DDOS massivo.
[ 0x05 ] THE_DEBUG_LOG (REAL_WORLD_EXFIL)
Aqui está o que é extraído de um ataque real. Esqueça nomes de usuários bonitinhos; os bots tentam o que é padrão em ambientes Ubuntu, Web e Admin.
No log abaixo, capturado em 2025-07-18, vemos um atacante de Hong Kong (47.238.151.234) usando libssh2_1.11.1 para realizar um brute-force em série. O tempo de conexão? Apenas 0.6 segundos. Isso indica um scanner em massa, automatizado para testar e descartar alvos em milissegundos.
2025-07-18T02:06:15+0000 [SSHTransport,47.238.151.234] login attempt [ubuntu/qwe123456] failed
2025-07-18T02:06:18+0000 [SSHTransport,47.238.151.234] login attempt [web/P@ssw0rd] failed
2025-07-18T02:07:09+0000 [SSHTransport,47.238.151.234] login attempt [adam/adam123] failed
2025-07-18T02:07:19+0000 [SSHTransport,47.238.151.234] login attempt [app/111111] failed
2025-07-18T02:07:50+0000 [SSHTransport,47.238.151.234] login attempt [demo/demo] failed
[ 0x06 ] ANOMALY_DETECTED: PUBLIC_KEY_ATTACK
Nem tudo é brute-force de senha. Atacantes mais avançados tentam injetar chaves públicas ou usar credenciais vazadas de repositórios expostos.
Recentemente, o IP 182.92.11.80 tentou uma conexão usando a public key para o usuário NL5xUDpV2xRa. O ataque foi tão agressivo ou mal-formado que chegou a causar um exceção interna no honeypot. Quando o atacante começa a tentar chaves específicas, o jogo muda: ele não está mais apenas batendo na porta; ele está tentando usar a chave mestre de um vazamento anterior.
[ 0x07 ] SURVIVAL_GUIDE: HARDENING_101
Não adianta chorar no Twitter/X. A internet é hostil. Se você quer parar de ser um "pontinho vermelho" no mapa de alguém, o checklist é obrigatório:
- Kill Passwords: Se você usa senha no SSH, você já perdeu. Use Ed25519 Keys.
- Move the Gate: Mudar a porta 22 para algo como 49152 ajuda? Sim, mas só contra scripts burros. Shodan vai te achar de qualquer jeito.
- Active Defense: Instale CrowdSec. Ele é como um Waze para ataques: se um IP atacou alguém na rede deles, ele já chega banido no seu servidor.
- Audit Your IoT: Se o seu roteador não recebe update desde 2021, ele não é um roteador, é um membro da botnet de alguém.
[ 0x08 ] MASSIVE_RECON: NMAP_ON_STEROIDS
Como que esses caras te acham em menos de 1 minuto? Simples: velocidade bruta.
Olha esse scan abaixo. Foram testados 4096 endereços IP em apenas 3.58 segundos. Usando taxas de pacotes agressivas (--min-rate 5000), um atacante consegue varrer sub-redes inteiras atrás de portas específicas (como a 25565 de Minecraft ou a 22 de SSH) em tempo recorde.
# sudo nmap -n -Pn -T5 --min-rate 5000 --open -p 25565 152.67.32.0/20 -vvvv
Scanning 4096 hosts [1 port/host]
Discovered open port 25565/tcp on 152.67.32.10
Discovered open port 25565/tcp on 152.67.34.19
Nmap done: 4096 IP addresses scanned in 3.58 seconds
Raw packets sent: 8175 (359.700KB) | Rcvd: 19 (928B)
Se você tem uma porta aberta, você é apenas um bit num scan de 3 segundos de alguém. Não é pessoal, é estatística.
[ 0x09 ] TARGET_ANALYSIS: VULNERABLE_TOMCAT_7.0.92
Depois que o scan termina, o atacante agora tem uma lista de IPs "vivos". Um exemplo real? O IP 152.67.33.53:8080 rodando um Apache Tomcat/7.0.92.
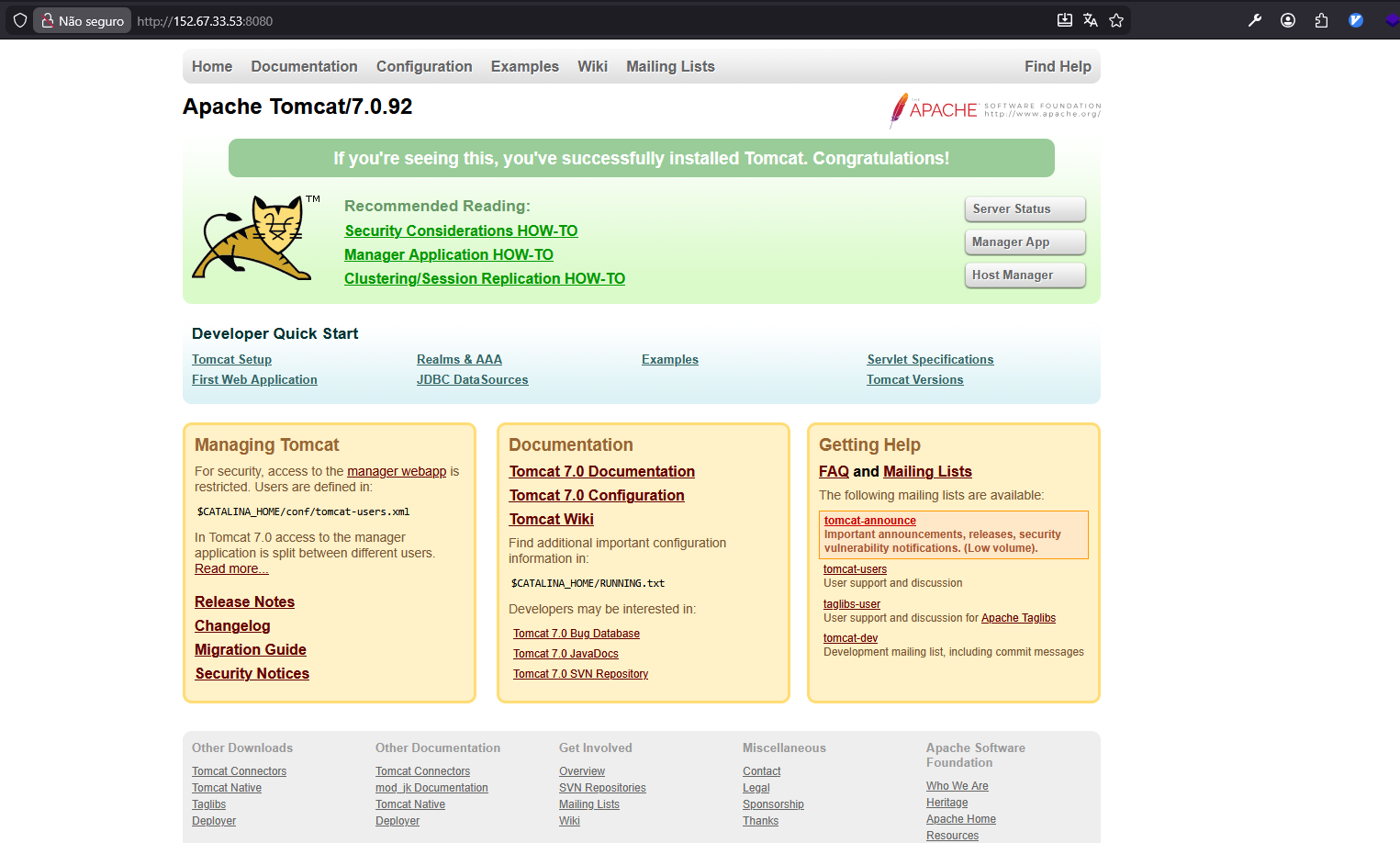
Essa versão é um "parque de diversões" para o Red Team. Só de olhar o versionamento, já sabemos que ele está aberto para:
1. Ghostcat (CVE-2020-1938): Permite ler arquivos internos (configurações) via porta AJP (8009).
2. RCE via CGI Servlet (CVE-2019-0232): Se estiver em Windows, injeção de comandos via .bat.
3. Manager App: Versões antigas são alvos constantes de brute-force para upload de arquivos .war maliciosos (WebShell).
Encontrar o alvo demorou 3.70 segundos. O que vem depois é apenas execução técnica.
[ 0x0A ] FINAL_THOUGHTS
O mapa vermelho da internet não é sobre você. É sobre a exploração massiva de recursos computacionais. Entender que você está sendo escaneado neste exato momento não é paranoia.
A pergunta de ouro no Red/Blue Team não é se você vai ser invadido, é: "O quanto de barulho o atacante vai ter que fazer antes de eu dar um 'shutdown' na conexão dele?".
Fique seguro, use chaves, e pare de usar admin/admin pelo amor de Deus kkkkk.
